The biggest most damaging and most widespread threat facing small businesses are phishing attacks.
Most common cyber security threats facing organisations today.
Some types of threats are more invasive than others but they can all be equally jarring for a business left unprepared.
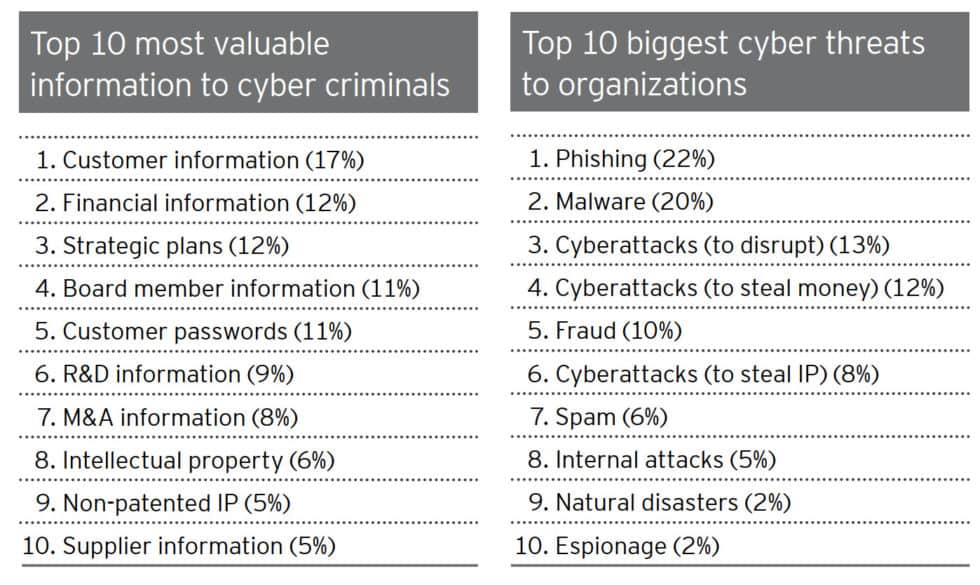
Phishing accounts for 90 of all breaches that organizations face they ve grown 65 over the last year and they account for over 12 billion in business losses.
A cyberattack is a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization.
We ve covered the history of web exploiting and the biggest exploits the world has experienced but today we re going back to basics exploring and explaining the most common network security threats you may encounter while online.
What are the most common cyber attacks.
Here s a list of cyber security threats that most businesses contend with on a daily basis whether they realize it or not.
However the risk is still high.
As to the methods used by those with malicious intent weaknesses in the application such as.
The most common issues that arise tend to fall around company devices being used for non work purposes or in fact for work but in insecure locations.
A few of the typical attackers and sources of cybersecurity threats include.
As cyber criminals become increasingly sophisticated and cybersecurity threats continue to rise organizations are becoming more and more aware of the potential threat posed by third parties.
We ve all heard about them and we all have our fears.
The potency and frequency of today s cyber threats requires a security strategy build on the assumption of compromise.
9 cyber security threats faced by big businesses.
Cyber security is a vital component of every companies infrastructure.
Regardless of size scope or industry every company that wants to survive must answer two fundamental questions.
What are the most common cybersecurity threats for businesses.
App attacks the most common type of data breach.
Top five security threats facing your business and how to respond.
A network or device may not be breached today but remains at risk so the process of protecting detecting and responding to a breach is a continuous one.
Today cyber attacks can come from a variety of places and in a variety of forms.
Usually the attacker seeks some type of benefit from disrupting the victim s network.
You may believe that this should still come under compliance of cyber security policies however it does need to be addressed as a separate threat.
Success depends on a company s ability to protect its proprietary information and customer data from those who would abuse it.